PhishX
is a python tool that can capture user credentials using a spear
phishing attack. Spear phishing is a targeted form of phishing attack
that is launched against specific individuals. Therefore, some
information about an individual is required in order to launch such an
attack. Since PhishX is used to capture user’s credentials, the tool
generates fake pages and adds target information to said pages. The
pages are shared with the target users. If the users share any data on
the fake pages, the information is captured by the interface on the
attacker’s machine. The pages that can be used (cloned) for spear
phishing attack include Facebook, Google, Twitter, Instagram, LinkedIn,
Pinterest, Quora, and Steam. All the available pages support the mobile
version except LinkedIn.
PhishX Installation
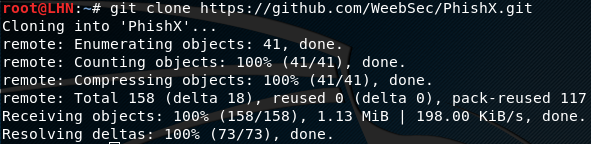
PhishX works with Kali Linux and Parrot-Sec OS. To install PhishX,
clone the tool from Github repository using the following command.
git clone https://github.com/WeebSec/PhishX.git
After cloning, run the following commands to install the tool and its requirements.
cd PhishX
chmod +x installer.sh
bash installer.sh
Running PhishX
Run the PhishX tool using the following command.
python3 PhishX.py
The above command loads the PhishX interface with the page options that can be used for spear phishing, as shown below.
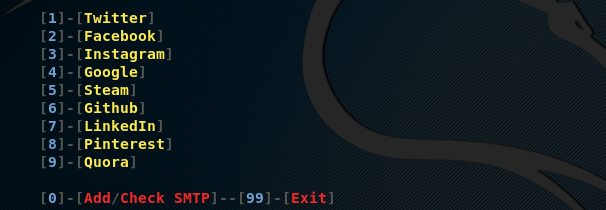
We can select any page format by typing its sequence number. For
instance, we can select the Google page option by typing the sequence
number 4 in the terminal. This opens the Google page setup for said
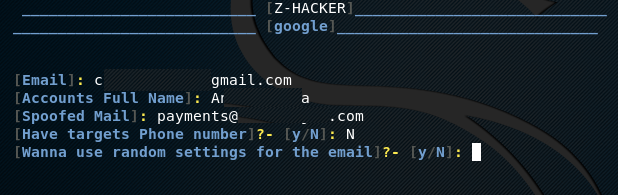
spear phishing attack. As mentioned earlier, the spear phishing attack
requires target information. For Google page phishing account, the tool
asks for target information like email address, user name, phone number
(optional), and location (if known). The tool also asks for the spoofed
email.
Once the information is provided, the tool generates a link that can
be shared with the user via any preferred technique. An interface on the
attacking machine listens for user activity on the shared link. The
link contains a Google account login page, as shown in the following
screenshot.
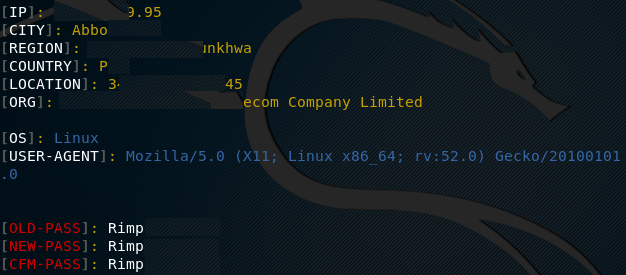
If the user tries to log into the Google account, the credentials are
captured by the tool along with other information like user location
and IP address.
![Author Image]()






Aucun commentaire:
Enregistrer un commentaire